In a digital ecosystem where the lines between innovation and threat are blurring by the second, the Security Operations Centre (SOC) is emerging as the strategic nerve centre of every modern organisation. It is no longer just a technical bastion monitoring alerts, but a dynamically evolving organism that must stay ahead of the movements of increasingly sophisticated adversaries. In an age of AI-driven attacks and ubiquitous cloud, the effectiveness of the SOC determines the survival, reputation and continuity of the business.
Pillars of cyber defence: the synergy of people, processes and technology
The effectiveness of any SOC rests on the harmonious cooperation of three fundamental pillars: skilled people, standardised processes and advanced technology. Neglecting any of these creates gaps that become open gates for attackers.
People – the irreplaceable heart of the operation
It is the people – their knowledge, intuition and ability to think analytically – that are the most important element of cyber defence. The SOC team is usually a multi-level structure, where each line has clearly defined tasks. L1 analysts are the front line, monitoring the constant flow of alerts 24/7, filtering out information noise and escalating potential threats. L2 analysts, incident specialists, perform in-depth analysis, determine the scale of the attack and implement countermeasures. At the top are L3 analysts – elite ‘threat hunters’ who proactively look for signs of advanced, hidden adversaries. The whole is supported by security engineers, responsible for the architecture and maintenance of the tools, and a SOC manager, who manages the strategy and the team.
Processes – the backbone of effectiveness
Standardised processes ensure consistency and repeatability of actions, regardless of time pressures or shift composition. This is based on the NIST incident lifecycle, which defines four key phases: preparation, detection and analysis, containment and eradication, and post-incident action, or lessons learned. Mature SOCs complement this reactive model with proactive threat hunting – the iterative process of searching the network for signs of adversaries that have evaded automated defences.
Technology – the arsenal of the modern defender
A modern SOC is based on an integrated ecosystem of tools. At its heart is the SIEM (Security Information and Event Management) system, which aggregates and correlates logs from across the infrastructure, acting as the analytical brain of operations. SOAR (Security Orchestration, Automation, and Response) platforms act as a ‘force multiplier’, automating repetitive tasks and orchestrating incident response, allowing analysts to focus on more complex problems. EDR (Endpoint Detection and Response) technologies, providing deep visibility into workstations and servers, and its evolution, XDR (Extended Detection and Response), which integrates data from multiple layers (network, cloud, email) to offer a holistic view of the attack, also play a key role.
A vicious circle of challenges: fatigue, skills gap and complexity of risks
Despite advanced tools, SOC teams around the world are facing an operational crisis driven by three interrelated challenges.
The first is alert fatigue (alert fatigue). Large organisations can receive up to tens of thousands of alerts a day, more than half of which are false alarms. This constant ‘noise’ leads to desensitisation and job burnout – more than 70% of analysts report symptoms of it. Paradoxically, the more alerts, the less security, as the risk of overlooking that one critical signal of a real attack increases.
The second challenge is the global skills gap. It is estimated that there is a global shortage of around 4 million cyber security professionals. In Europe, 61% of teams are understaffed and nearly half of companies have serious recruitment difficulties. In Poland, 27% of companies report problems finding IT experts, including cyber security experts. Talent shortages lead to overloading existing teams, which in turn fuels burnout and turnover, creating a vicious circle.
The third element is the increasing complexity of the threat landscape. The migration to the cloud has opened up new attack vectors, where as many as 99% of incidents are due to client-side configuration errors. At the same time, cybercriminals are increasingly daring to use artificial intelligence to automate and personalise attacks – from generating linguistically flawless phishing emails, to creating polymorphic malware, to deepfakes used in financial fraud.
Next-generation SOC: intelligent automation and proactive defence
In response to these challenges, the SOC is undergoing a fundamental transformation in which artificial intelligence is playing a key role – not as a replacement for humans, but as their most powerful ally.
AI and machine learning (ML) algorithms are becoming the first line of defence against alert fatigue. They can analyse huge datasets in real time, automatically reject false alerts, and enrich the relevant ones with context and prioritisation. Technologies such as User and Entity Behaviour Analysis (UEBA) learn the ‘normal’ functioning of the environment and flag any anomalies that might escape human attention.
The latest wave, generative AI, is revolutionising the work of analysts. Tools such as Microsoft Security Copilot and Splunk AI Assist can translate natural language queries into complex code, automatically generate concise summaries of complex incidents and recommend next investigative steps. This frees analysts from routine tasks, allowing them to focus on strategic thinking and verification of AI results. The role of the analyst is evolving from ‘tool operator’ to ‘AI supervisor and partner’.
This technological evolution is also driving a strategic paradigm shift – from reactive to proactive defence. Instead of waiting for an alert, the next-generation SOC proactively manages risk. It implements strategies such as Continuous Threat Exposure Management (CTEM), systematically identifying and prioritising vulnerabilities from a business perspective. AI here supports advanced threat hunting, automating hypothesis generation and scouring data for subtle signs of compromise.
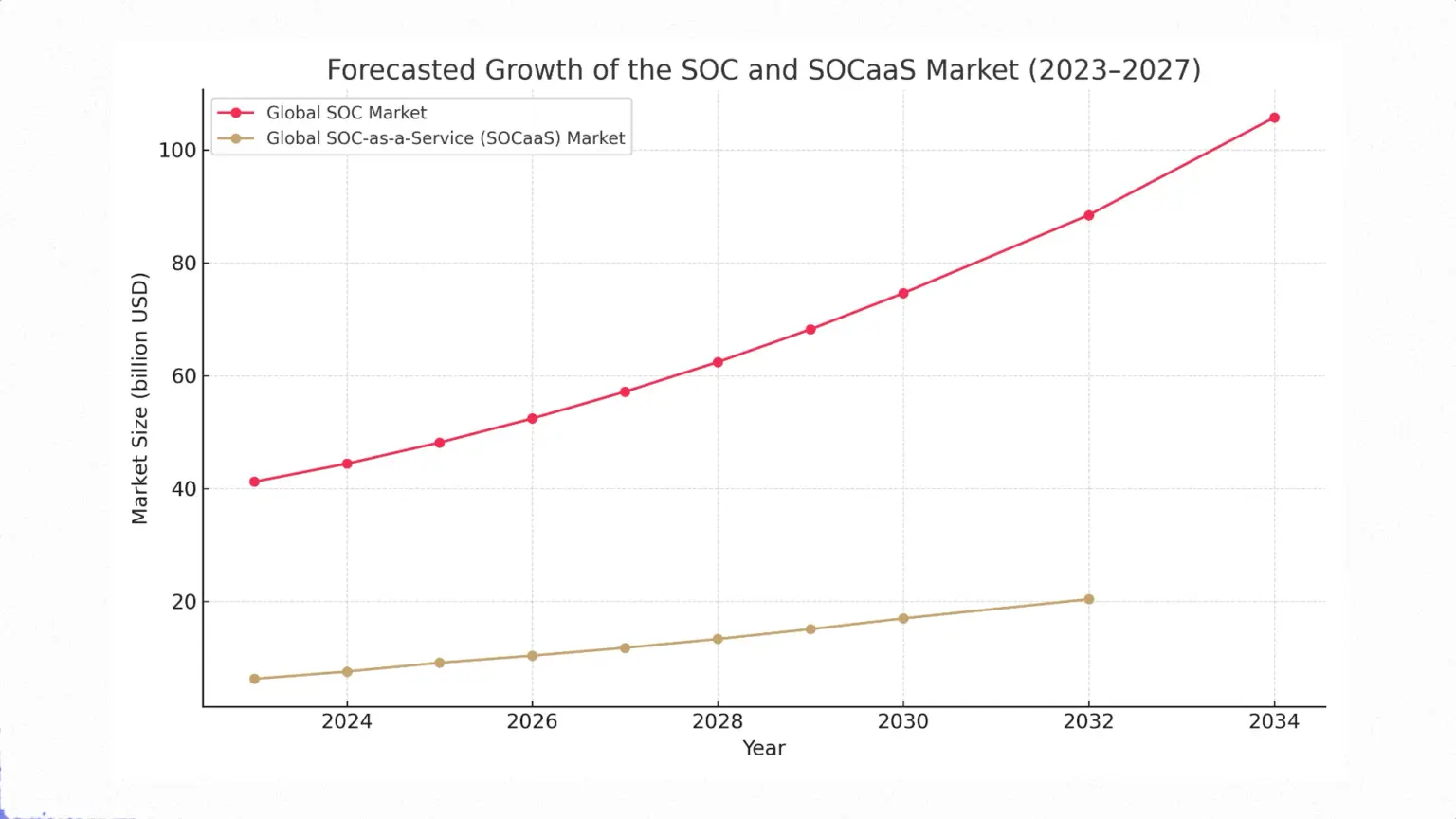
Catalysts for expansion: Key factors shaping the SOC market
Behind the impressive growth figures for the Security Operations Centre market is a set of powerful and interrelated driving forces. Understanding these drivers is key to assessing the sustainability of current trends and predicting the future evolution of the industry. This section explores the fundamental reasons why organisations around the world are investing with increasing urgency and scale in advanced defence capabilities.
The evolving threat landscape: A new era of adversaries
The primary driver of the SOC market is the constant and accelerating evolution of the threat itself. Modern cyber attacks have long ceased to be the domain of individual hackers; they have become a highly organised, automated and profitable branch of crime. We are seeing a fundamental shift in the characteristics of threats, which are becoming increasingly complex, persistent and destructive. Organisations no longer face just simple malware, but advanced, multi-vector campaigns such as Advanced Persistent Threats (APTs) and ransomware attacks that can cripple entire enterprises.
This technological escalation on the attackers’ side forces a corresponding response on the defenders’ side. Traditional, reactive and signature-based security mechanisms are becoming insufficient. The need to detect subtle anomalies, analyse complex behaviour patterns and respond in machine time is directly driving the demand for modern SOCs equipped with AI and machine learning-based analytical tools.
Digital transformation and the expanding attack surface
In parallel to the evolution of threats, the very structure of corporate IT environments is undergoing a fundamental transformation. Digital transformation initiatives, while crucial to competitiveness, inevitably lead to a broadening and dispersal of the attack surface, generating new and complex challenges for security teams.
Migration to the cloud: The mass movement of resources and applications to public clouds (AWS, Azure, GCP) and hybrid environments is one of the most important technology trends of the decade. However, this process is leading to the blurring of the traditional, well-defined network ‘perimeter’. Cloud security is based on a shared responsibility model, in which the cloud provider is responsible for the security of the platform itself, but the customer is fully responsible for the secure configuration of services, identity and access management and data protection. Unfortunately, misconfigurations of cloud services have become one of the main causes of data leaks. As Gartner analysis shows, as many as 99% of cloud security incidents are the result of customer-side error. This complexity and risk requires specialised tools and competencies in cloud configuration monitoring (CSPM) and cloud workload protection (CWPP), which are an integral part of a modern SOC. Case studies, such as the Capital One data leak caused by a misconfigured web application firewall in AWS, vividly illustrate the scale of this risk.
The proliferation of IoT and OT: Another factor is the convergence of information technology (IT) with operational technology (OT) and the explosive growth of Internet of Things (IoT) devices. OT systems, such as industrial control systems (ICS) and SCADA, which manage processes in factories, power plants or critical infrastructure, have historically been isolated from corporate networks. Their connection to the internet to optimise operations creates new critical attack vectors. Similarly, millions of IoT devices – from smart sensors to cameras – are introducing new endpoints into the corporate network that are often poorly secured, lack the ability to install security agents and are difficult to manage. Monitoring such a diverse and vast ecosystem of devices is impossible without the centralised analytics platform that SOC offers.
Increasing burden of compliance and risk management
The third pillar driving the growth of the SOC market is the increasingly complex and demanding regulatory environment and the increasing demands from business partners, including insurers. Having a documented capability to monitor and respond to incidents is no longer good practice and is becoming a hard business requirement.
It can be seen that these three key drivers – threat evolution, digital transformation and regulatory pressure – do not operate in isolation. They form a mutually reinforcing loop. Business initiatives such as migration to the cloud are creating new, complex attack surfaces. These new vectors are immediately exploited by adversaries armed with increasingly sophisticated tools such as AI. Increasing risks and spectacular incidents are attracting the attention of regulators and insurers, who are responding with stringent new requirements. For organisations, the only rational way to manage these complex risks, meet regulatory requirements and satisfy the expectations of business partners becomes to implement or hire a professional Security Operations Centre. In this way, business and technology decisions directly and indirectly drive demand in the SOC market.