Traditional security models are no longer effective. The ‘castle and moat’ concept – assuming that everything inside the corporate network is secure and that threats lurk only outside – has become outdated and inadequate to modern realities. In a world where data and applications leave the physical boundaries of an organisation and users connect to resources from anywhere in the world, the role of the firewall as the main line of defence is becoming irrelevant.
This is why the Zero Trust concept was born – not so much a new technology, but a complete change in the way we think about security. Its foundation is the principle of ‘never trust, always verify’. In practice, this means that any attempt to access resources, whether from an internal or external network, is treated as a potential threat and requires thorough verification.
From concept to standardised architecture
The term ‘Zero Trust’ was first used by John Kindervag of Forrester Research in 2010. In his view, building trust solely on the basis of network location is flawed by design. However, it was not until the publication of NIST document SP 800-207 that the concept was formalised and turned into a precisely defined security architecture.
Zero Trust according to NIST is based on several key assumptions. All data and services are treated as resources requiring protection, regardless of their location. All communications must be properly secured and access is granted on a session-by-session basis. Decisions to grant access are dynamic and dependent on a number of factors – including the identity of the user, the state of the device, and the context of the operation. Furthermore, organisations must monitor the integrity of resources, apply continuous identity verification and seek to automate and improve security mechanisms.
At the heart of this concept is the assumption that security breaches are inevitable – they can come from either outside or inside the organisation. This model completely rejects the idea of a trusted internal network.
Business value: safety, efficiency and savings
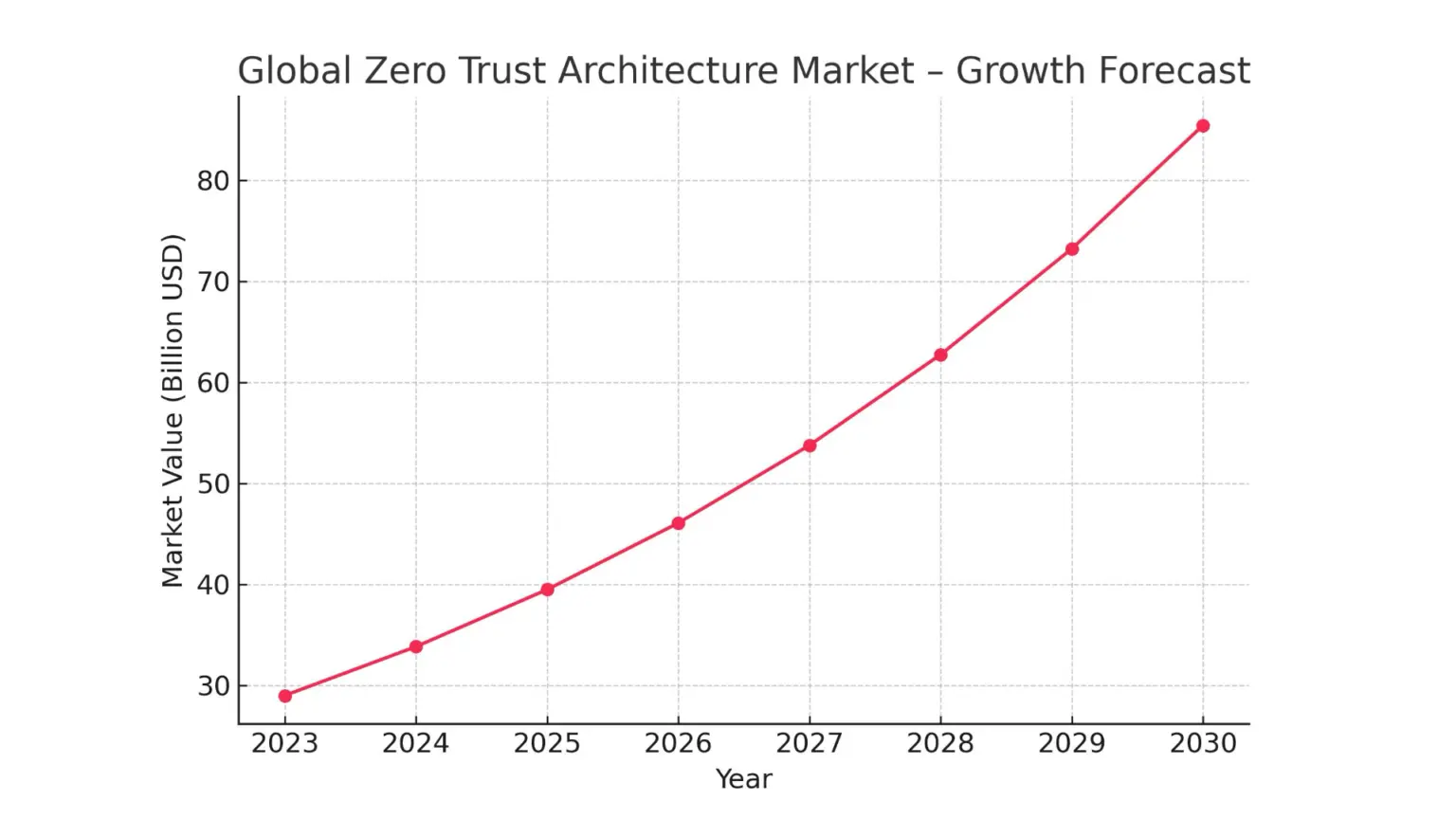
Zero Trust is not just a response to changing threats – it is also a sound business decision. The value of the Zero Trust solutions market is growing rapidly and is forecast to reach more than $85 billion by 2030, almost triple that in 2023.
The real benefits of implementing this strategy are confirmed by studies such as the Total Economic Impact™ report prepared by Forrester for Microsoft. It shows that implementing Zero Trust can reduce the risk of a data breach by up to half, deliver a 92% return on investment over three years and significantly increase the productivity of security teams. Additionally, organisations save millions of dollars by consolidating tools and simplifying their IT infrastructure. At the same time, companies implementing Zero Trust are less likely to fall victim to successful cyber attacks, and can more easily comply with regulatory requirements under regulations such as RODO, NIS2 and DORA.
Zero Trust’s technological foundations
For a Zero Trust strategy to work effectively, it needs to be based on several closely interlinked technological pillars. The first is **identity** – in the modern IT environment, it is the user and their identity that is becoming the new security perimeter. Solutions such as multi-factor authentication, single sign-on and context-sensitive access mechanisms to dynamically assess the level of risk are key here.
Another element is the end devices. Any laptop, smartphone or server can become an entry point for threats, so their status must be constantly monitored. Technologies such as endpoint management (UEM) or incident detection and response (EDR) systems make it possible to keep devices in line with security policies.
The network, in turn, should be segmented in a way that prevents unauthorised users from moving freely between resources. The modern approach to connectivity is based on ZTNA-type solutions that allow secure, individual user connections to a specific application, hiding the rest of the infrastructure.
Applications and data deserve just as much attention – they are the ultimate target of cyber attacks. Protecting them effectively requires data classification, the use of leakage prevention mechanisms (DLP) and encryption of information both at rest and during transmission.
Last but not least, visibility and automation is a key pillar. Integrated analytics systems, such as SIEM and SOAR, collect data from across the IT environment and enable the rapid detection of threats. The use of machine learning in user behaviour analytics (UEBA), on the other hand, identifies unusual activities that may be indicative of a security breach.
Implementation as an evolution, not a revolution
Zero Trust is not a project that can be completed by a specific date. It is an ongoing, strategic journey that requires consistency, commitment and an adaptive approach. The key to success is to start with areas that can deliver quick and measurable results, such as implementing SSO and MFA or replacing outdated VPN solutions with ZTNA. It is also necessary to take an inventory of assets and identify key data and systems – the so-called ‘crown jewels’.
Artificial intelligence and convergence with SASE
The Zero Trust architecture is constantly evolving. Artificial intelligence and machine learning are playing an increasingly important role, supporting anomaly detection, risk analysis and incident response automation. The integrated approach to security is also reflected in the concept of SASE – an architecture that combines network functions with security services and delivers them as a single, cloud-based service.
Zero Trust defines ‘what’ and ‘why’ we secure. SASE answers the question of ‘how’ we implement it. Observing the market, there is a clear trend towards consolidation – by 2029, most companies will be using SASE solutions from a single vendor, significantly simplifying security management.