Russian military intelligence was behind December’s cyber attack on Poland’s critical infrastructure
The December attempt to attack the Polish power grid using the destructive DynoWiper malware marks an escalation of digital confrontation…
Russian military intelligence was behind December’s cyber attack on Poland’s critical infrastructure
The December attempt to attack the Polish power grid using the destructive DynoWiper malware marks an escalation of…
Logitech confirms attack. Customer and employee data at risk after Oracle vulnerability
Logitech has confirmed a security incident in which hackers gained access to company, customer, and supplier data. The…
EY’s 4TB backup leak. What this incident teaches
The leak of 4 TB of EY backups is yet another example of how companies still fail to…
F5 hacking attack. The giant admits: Breach will hurt demand.
F5 is facing serious consequences from a recent major breach of its own systems. In response to the…
Cyber attacks accelerate: criminals steal data in as little as half an hour
Cyberattacks are becoming faster, more automated, and powered by artificial intelligence. New data from Palo Alto Networks shows…
F5 hacked: Risks to global networks and IT infrastructure
The attack on F5, one of the key providers of cybersecurity solutions, shows that even the guardians of…
Arrests after cyber attack on Kido nurseries. Hackers stole data of 8,000 children
British police have arrested two people in connection with a ransomware attack on the Kido International nursery chain,…
Anatomy of a zero-day attack: How hackers exploit unknown vulnerabilities and how to defend against it?
Attackers have changed their strategy, targeting not millions of users, but the heart of corporate infrastructure through unknown…
Renault: Customer personal data stolen in cyber attack on third-party company
Renault UK has confirmed a customer data breach following a cyberattack on one of its external suppliers. The…
Cyber attack on Salesforce customers. Hackers claim to have taken over one billion records
A cybercriminal group calling itself “Scattered LAPSUS$ Hunters” claims to have stolen nearly a billion records belonging to…
Cyber attack on software provider paralyses key European airports
A ransomware cyberattack on an aviation software provider paralyzed operations at key European airports from London to Berlin…
Hybrid threat: How drones over Poland translate into cyber risk
Analysis of Russian services' strategies and forecast of threats to the Polish IT sector and critical infrastructure.
Akamai Technologies warns: 4-step blackmail defines the new face of ransomware
Double extortion in ransomware attacks is no longer enough for cybercriminals, who are escalating to a four-phase blackmail…
The lost innocence of the web: the story of the first great cyber attack
On November 2, 1988, a program consisting of just 99 lines of code, written by a single student,…
Clickjacking as part of the attack chain: an underestimated threat in security architecture
Clickjacking has remained on the periphery of security departments' attention for years - regarded more as a threat…
Why every cable in a factory today is a potential entry point for a hacker
Just a decade ago, the industrial production line was a closed world. Machines ran on isolated networks and…
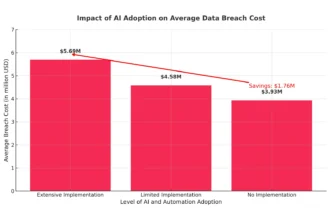
AI in cyber security, or how to save $1.76m and reduce attack response by 108 days
Every IT leader and security director knows this scenario all too well: the endless stream of security alerts,…
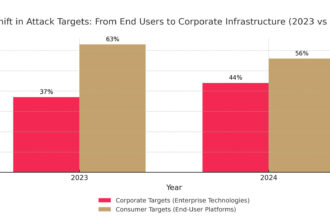
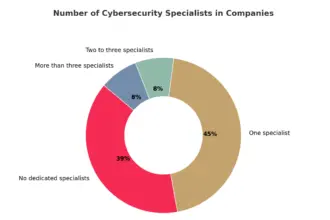
Poland’s alarming skills gap. Why are we such an easy target for hackers?
Poland's economy is at the heart of a digital paradox. On the one hand, the country is dynamically…
The more tools, the worse? The cyber security paradox that is destroying businesses
Companies are investing in dozens of tools to protect their growing infrastructure. However, this intuitive action creates a…
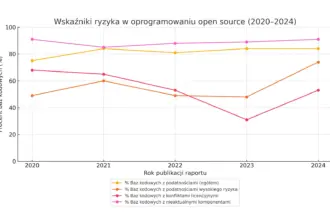
The Open Source Paradox – How innovation became the biggest threat to business
Oprogramowanie open source stało się fundamentem współczesnych aplikacji – odpowiada dziś średnio za 77% całego kodu w rozwiązaniach…
Cyber insurance is not enough. Why don’t policies cover real losses after an attack?
More and more companies are investing in cyber insurance, seeing it as the last line of defence against…