The end of cheap power for AI? Trump hits back at tech giants
The White House is challenging tech giants, effectively turning the largest consumers of electricity into compulsory developers of energy infrastructure.…
The end of the fortress era. Why is cyber resilience the future of IT?
The scale and sophistication of cyber threats in Poland necessitates a fundamental change in the approach to IT…
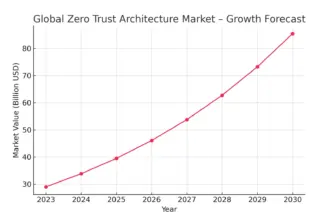
Cyber Security 2025: How many companies have really implemented Zero Trust?
In 2025, the world of cybersecurity is dominated by Zero Trust, but the growing popularity of this philosophy…
Why every cable in a factory today is a potential entry point for a hacker
Just a decade ago, the industrial production line was a closed world. Machines ran on isolated networks and…
An investment that pays off – implementing Zero Trust architecture
Traditional security models are no longer effective. The 'castle and moat' concept - assuming that everything inside the…
Remote working must go hand in hand with IT asset security (interview)
Recently, there has been a sharp increase in interest in remote working due to the epidemiological threat. However,…