Every IT leader and security director knows this scenario all too well: the endless stream of security alerts, the growing fatigue of the analytics team (so-called alert fatigue), the acute shortage of specialists in the market and the relentless pressure to optimise budgets. In such a demanding environment, relying solely on manual threat analysis is becoming an inefficient and dangerous model. Cybercriminals are already using artificial intelligence and automation on a massive scale to type targets, create highly personalised phishing attacks and rapidly bypass traditional defences . Attempting a defence based solely on human response is doomed to failure in advance – it is too slow, too costly and too error-prone.
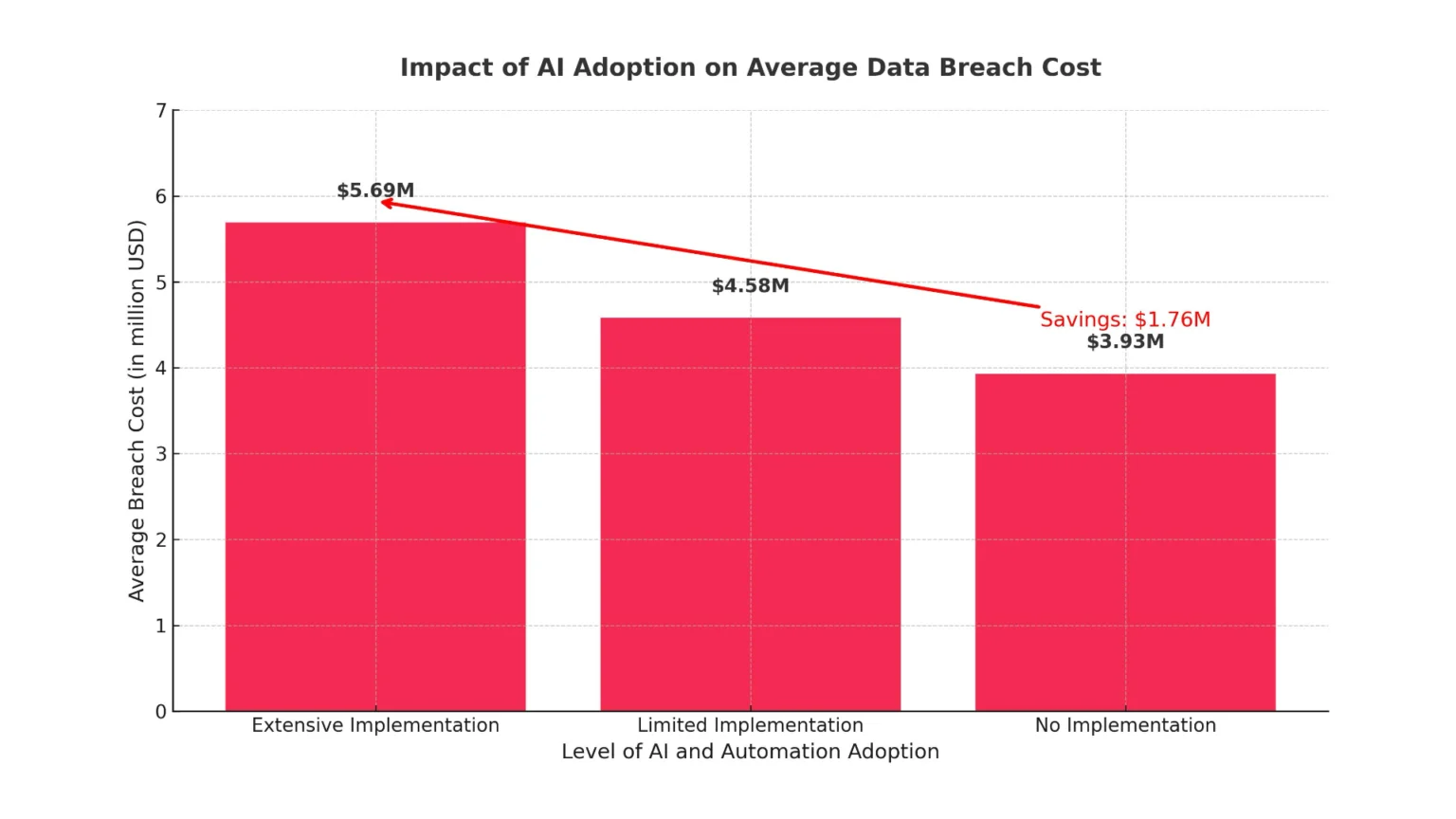
However, recent data shows that there is a measurable and highly effective answer to this challenge. A key finding from IBM’s‘Cost of a Data Breach 20235‘ report is clear: the use of AI and automation is the #1 factor that most strongly reduces the financial impact of a security breach. In this article, we’ll explore where the $1.76 million saving comes from and how reducing the attack lifecycle by 108 days translates into real benefits for your organisation.
Investment with the highest return on investment (ROI)
When analysing the factors that have the greatest impact on minimising financial losses after an incident, the data leaves no illusions. Investing in intelligent automation is simply the most cost-effective strategy for building cyber resilience. IBM’s 2023 report, compiling the factors that mitigate the costs of a breach, makes the point clear. Implementing AI and automation is at the top of the list, offering the greatest reduction in potential losses. Significantly, this factor even surpasses such fundamental elements as having a dedicated Incident Response Team or using well-established DevSecOps practices.
The figures speak for themselves. An average saving of USD 1.76 million is the difference in the cost of breach between organisations with fully implemented AI systems and those that do not use them at all. In the former group, the average cost was US$3.93m, while in the latter it was as high as US$5.69m. This is the largest single saving identified in the entire study, making AI and automation the investment with the highest documented return.
Although these amounts seem huge, the principle of proportion is universal. For a Polish e-commerce company, software house or manufacturing plant, a reduction in potential losses of more than 30% can mean the difference between surviving the crisis and bankruptcy. This is not an abstract statistic for global corporations, but a hard indicator of strategic maturity. This is particularly relevant in the context of the Polish market, which is facing an alarming shortage of cyber-security specialists, estimated at between 10,000 and 17,500 people, while demand for these competences is growing at the highest rate in Europe (36% year-on-year). Moreover, as many as 39% of Polish companies do not employ a single employee responsible for cyber security, creating ideal conditions for attackers.
Time is money: how AI shortens the attack lifecycle by more than 3 months
A second, equally key dimension of benefit is the drastic reduction in exposure time to an active threat. Organisations that make full use of AI and automation identify and stop attacks on average 108 days faster than companies that do not (214 days vs 322 days). That’s a difference of more than three months that has a direct cost impact.
Why such a powerful difference? The mechanism is simple and is based on the synergy of two key technologies:
- Detection at the speed of the machine (UEBA): AI does what humans will never be able to do – analyse billions of events from system logs, network traffic and endpoints in real time. Advanced User and Entity Behaviour Analytics (UEBA) modules build patterns of normal behaviour for every user and device on the network. This allows them to detect subtle anomalies – such as logging in from an unusual location at an unusual time, accessing rarely used files or attempting to escalate permissions – that would easily escape an overloaded analyst . It is these deviations from the norm that are often the first sign of an advanced attack.
- Real-time response (SOAR): Once an anomaly is detected, automation comes into play, usually in the form of SOAR (Security Orchestration, Automation, and Response) platforms . It allows an immediate, predefined response – e.g. automatically isolating an infected workstation from the network, blocking a suspicious user account or running a detailed scan – without waiting for human intervention . This eliminates the most costly element in the response chain: delay.
It is important to remember that each additional day of active breach represents an increasing cost: more stolen or encrypted data, longer and more severe operational downtime, greater reputational damage and rising legal and crisis communications costs. The IBM report confirms this correlation, showing that breaches lasting more than 200 days cost, on average, more than US$1 million more than those contained below this threshold.
Which AI technologies to implement in the company?
The question that naturally arises is “OK, what specifically should I invest in?”. Implementing AI and automation is not a monolithic project, but a process that can be pursued by integrating specific classes of solutions.
Here are the key technologies driving this revolution:
- SIEM / XDR with behavioural analytics (UEBA): The brains of operations. Modern SIEM (Security Information and Event Management) and XDR (Extended Detection and Response) systems enhanced with UEBA modules become the focal point for analysing, correlating and detecting advanced, hidden threats.
- SOAR (Security Orchestration, Automation, and Response): This is the nervous system that turns detection into action. SOAR platforms automate repetitive tasks and entire response procedures (playbooks) by integrating different security tools and orchestrating their joint response.
- Modern EDRs (Endpoint Detection and Response): These are automatic gatekeepers on workstations and servers. EDR systems use AI to block malware, analyse attack techniques and automatically roll back malicious changes.
- AI in data protection (DLP): Traditional Data Loss Prevention (DLP) systems based on simple rules often fail. Modern solutions use AI to understand the context and content of data, allowing for much more precise identification and protection of sensitive information, drastically reducing false positives.
- Identity Management (IAM): Intelligent IAM systems implement so-called adaptive multi-factor authentication (MFA). AI continuously assesses the risk of a given session and dynamically adjusts the authentication requirements, requesting additional verification only when necessary.
It is worth noting that many of these advanced solutions are today available in a flexible cloud model (SaaS) . This significantly lowers the entry threshold, eliminating the need for large, one-off capital investments (CAPEX) in favour of predictable, monthly operating costs (OPEX). For Polish companies, especially those in the SME sector, this is a historic opportunity to access technologies that only a few years ago were reserved for the largest global players.
Strategic context: Evolution of threats and defences
Analysis of the 2023 data provides a powerful argument, but the picture becomes even clearer when looking at the latest trends. Successive editions of the IBM report show that the role of AI is becoming even more critical.Evolving from Response to Prevention: 2024 report (analysing data from 2023-2024) reveals that the value of AI is shifting towards prevention. Organisations that used AI extensively in areas such as Attack Surface Management or proactive security testing reduced the average cost of a breach by US$2.2 million compared to companies not using these technologies . This is proof that the technology is maturing, allowing not only to put out fires faster, but to prevent them from happening in the first place.
New Risk – ‘Shadow AI’: The latest research introduces a worrying new term into the lexicon: “Shadow AI”. It refers to the uncontrolled use of AI tools by employees, without the knowledge or oversight of IT departments. Incidents in which ‘Shadow AI’ played a role cost companies an average of USD 670,000 more . As many as 97% of companies affected by an AI incident did not have appropriate access control mechanisms in place for these technologies .
This data leads to a fundamental conclusion. The risk is not the AI technology itself, but its uncontrolled, ‘wild’ application. This is a powerful argument for implementing a centralised AI governance model (AI Governance). The security team needs to evolve from a ‘braking’ role to a partner that enables AI-based innovations to be implemented safely.
The era when cyber security was based on manual analysis and reactive firefighting is irrevocably passing. The data clearly shows that the future – indeed the present – of a secure and resilient organisation lies in intelligent automation.
Conclusion 1 (Financial): Investment in AI and automation in cyber security delivers the greatest measurable return, reducing the average cost of a breach by US$1.76m.
Conclusion 2 (Operational): These technologies reduce risk exposure time by as much as 108 days, which directly translates into lower operational, financial and image losses.
Conclusion 3 (Strategic): AI is no longer a futuristic add-on, but a strategic necessity and the most effective way to build real digital resilience in the face of automated attacks and a critical shortage of specialists in the market .
The call to action for any IT leader is therefore simple: conduct an audit of your current technology stack. Evaluate in which areas – from detection to response to identity protection – the implementation of intelligent automation will yield the quickest and greatest benefits. It is no longer a question of ‘if’, but ‘when and how’ to use these technologies to defend your organisation. The time to act is now.