Palo Alto Networks and CyberArk 2026 merger: What does it mean for the cyber security market?
Finalizacja przejęcia CyberArk przez Palo Alto Networks to moment zwrotny, który przesuwa ciężar cyfrowej obrony z granic sieci bezpośrednio na…
Digital Trust is the new currency in IT. How Apple and Amazon turned privacy into billions in profits
The modern market is no longer an arena for competition based on product features, but rather a space…
Palo Alto Networks and CyberArk 2026 merger: What does it mean for the cyber security market?
Finalizacja przejęcia CyberArk przez Palo Alto Networks to moment zwrotny, który przesuwa ciężar cyfrowej obrony z granic sieci…
Anthropic hits the enterprise sector. Claude Opus 4.6 release with 500 CVE vulnerability detection feature
The launch of Claude Opus 4.6 signals that Anthropic is shifting its focus from simple text interactions to…
AI agents are the new potential vulnerabilities. How not to lose control of your company’s cyber security?
In 2026, artificial intelligence ceased to be merely a digital assistant, becoming an autonomous actor that independently makes…
The big leak from small screens. The smartphone is the weakest link in the payment chain
The rapid shift of Polish consumers towards m-commerce has made smartphones the central point of contact with capital,…
Lack of staff is no excuse. How do you build enterprise-class cyber security without an army of IT professionals?
Maintaining an efficient security department on your own is no longer just a technical challenge, but a critical…
You invest in firewalls and lose data through Teams. Time for a ‘Human Risk’ audit
While companies are building increasingly expensive digital fortresses, hackers have found the key to the back door, shifting…
Platformisation of cybersecurity in 2026: Strategic necessity or fashionable buzzword?
The long-standing dogma of combining the best but separate solutions has definitively collapsed under the weight of operational…
New Year’s Eve 2025: Farewell to the year of ransomware, hello to the year of deepfakes
The explosion of generative artificial intelligence capabilities has caused deepfakes to rapidly evolve from a technological curiosity into…
Cyber Security 2026: Why is the integration of IT, OT and IoT inevitable?
The evolution of cyber threats driven by artificial intelligence means that by 2026, the traditional division between office…
DORA, NIS2 and RODO: The end of the ‘handyman’ era in IT
In 2026, IT departments found themselves caught between the pressure to innovate and the crushing weight of new…
NIS2 is not a shopping list for IT. Why is technology alone not enough?
Treating the NIS2 directive solely as a technology shopping list is a strategic mistake that could cost companies…
ServiceNow targets record acquisition. $7bn for IoT security
ServiceNow is preparing for its boldest move in the cybersecurity market, finalizing talks to acquire startup Armis for…
Okta report: Europe lags behind Asia in adoption of modern MFA
Although 70% of employees already use multi-factor authentication, the latest data from Okta reveals a disturbing truth about…
AI hacking AI. Why can companies lose this arms race?
With the rapid integration of artificial intelligence into business processes, a new critical threat has emerged: autonomous models…
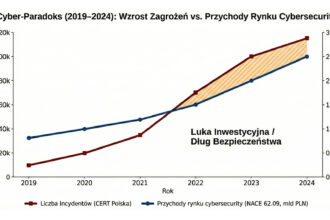
Cyber-Paradox: Why does the exponential increase in cyber attacks not translate 1:1 into security industry revenues?
The rapid escalation of cyber threats in Poland is not adequately reflected in the growth rate of the…
The end of the dictates of one model. Cyber security in 2026 will belong to hybrids and pragmatic AI
In 2026, the technical security industry will finally abandon the rigid division between cloud and local infrastructure, opting…
Drowning in alarms: why your SOC needs context, not data
Until recently, the IT industry believed that the key to digital security was collecting every possible byte of…
Phishing 2.0: Why are cyber fraudsters still one step ahead?
Once hackers, now criminal corporations. In the first half of 2025, CERT Polska registered over 100,000 phishing domains.…
Death of reactive defence. Trend Micro: Machines will attack faster than you can blink
By 2026, the cybercrime operating model will undergo a radical transformation, with human hackers being replaced by autonomous…
AI democratises cybercrime. Windows on target for hackers
The arms race in cyberspace has entered a new phase, with artificial intelligence becoming a key ally of…