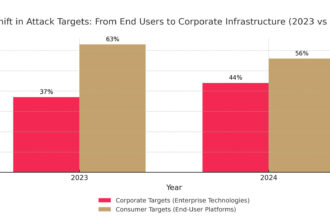
Anatomy of a zero-day attack: How hackers exploit unknown vulnerabilities and how to defend against it?
Attackers have changed their strategy, targeting not millions of users, but the heart of corporate infrastructure through unknown…
OpenAI chooses AMD. AI processor contract worth tens of billions
AMD has signed a groundbreaking, multi-year agreement to supply AI chips to OpenAI, posing a direct challenge to…
They sold LinkedIn data for $15,000. The backstory of the lawsuit against ProAPIs
LinkedIn has taken legal action against ProAPIs, accusing it of creating a vast network of bots to illegally…
Renault: Customer personal data stolen in cyber attack on third-party company
Renault UK has confirmed a customer data breach following a cyberattack on one of its external suppliers. The…
Pact with the devil or deal of the century? Hollywood and OpenAI sit down at the table on Sora
OpenAI is preempting potential legal disputes over its Sora video generation tool by offering film studios and copyright…
‘Uptober’ in full swing: bitcoin surpasses $125,000 and attracts institutional investors
Bitcoin is making history again, breaking through the psychological barrier of $125,000 and confirming its position as the…
Bezos knows how to cut data centre electricity bills. All it takes is a rocket and a few billion dollars
Jeff Bezos, founder of Amazon, envisions a future in which gigawatt data centers powering AI development leave Earth…
Cyber attack on Salesforce customers. Hackers claim to have taken over one billion records
A cybercriminal group calling itself “Scattered LAPSUS$ Hunters” claims to have stolen nearly a billion records belonging to…
AI bubble? Investors warn despite record funding for startups
Record amounts of venture capital are flowing into artificial intelligence startups, driving their valuations to astronomical levels. At…
The digital euro is getting closer. ECB bets on AI from Portuguese startup Feedzai
Europejski Bank Centralny zrobił kolejny krok w kierunku cyfrowego euro, wybierając portugalski startup Feedzai do stworzenia systemu wykrywania…
Qualcomm’s new chips based on Arm v9 – the answer to Apple and MediaTek competition
Qualcomm is reaching for the latest Arm v9 architecture, introducing a generation of chips optimized for AI computing.…
Apple is betting on smart glasses. Vision Pro loses priority
Apple is changing its strategy in the mixed reality segment, suspending development of the new version of the…
Nokia and Ericsson lose ground in China – Beijing bets on domestic 5G solutions
China is tightening its control over European telecommunications infrastructure suppliers, limiting Nokia and Ericsson's share in domestic networks.…
AI in everyday life: 5 applications you had no idea about
Artificial intelligence has become a quiet but ubiquitous architect of our everyday lives, operating far beyond commonly known…
Generation Z raised on the internet most likely to fall for phishing
Contrary to popular belief, the generation raised in the digital world turns out to be the weakest link…
AWS and NBA join forces: data, AI and new experiences for fans
Amazon Web Services and the NBA are strengthening their partnership by launching a new platform called Inside the…
Germany bets on AI and digitalisation to stifle bureaucracy and restore competitiveness
Germany is focusing on digitization and artificial intelligence as a remedy for years of slowdown and bureaucratic burdens…
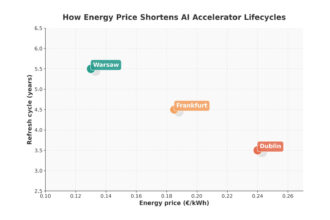
Megawatts to teraflops – how energy shapes AI hardware replacement cycles in the data centre
Rising electricity costs in European data center hubs are forcing operators to look more closely not only at…
From server rooms to AI gigafactories: the decade that changed data centres
Just a decade ago, data centers served as the invisible backbone of business—they ran applications and stored data,…
Not more people, just less complexity – that’s how CIOs are scaling today
IT teams are growing, projects are multiplying, and yet delivery speeds are falling—an increasingly common paradox in technology…
Machine learning after 60 years – from a game of checkers to a key tool in business IT
Machine learning has been around for over 60 years, but only today has it become one of the…