Palo Alto Networks warns: IT infrastructure replacement by 2029 is inevitable
While the tech industry is caught up in the AI gold rush, the CEO of Palo Alto Networks…
DDoS as a smokescreen. How hackers use chaos to quietly attack APIs and business logic
While headlines scream about record-breaking DDoS attacks exceeding 2 Tbps, the real threat has quietly moved elsewhere. This…
Cyber insurance: partner in crisis or just a payer?
Cyber insurance has become the most sought-after protection product for businesses. Today, companies expect policies to provide not…
Customers aren’t the only ones waiting for Black Friday. Nearly 90 hacking groups are taking aim at e-commerce
The approaching peak of the shopping season promises record revenues for online retailers. At the same time, it…
The slogan: ‘LOUVRE’. How technological debt and years of neglect have put the Louvre at risk
The recent theft of jewels from the Louvre revealed not only physical security gaps, but above all the…
Agent-based AI without governance. The most expensive technology mistake of the decade?
Agent AI promises an operational revolution, but most companies implement it randomly, without real oversight and without measurable…
AI as a weapon, a shield and a risk: How does the CISO need to change its strategy?
Artificial intelligence is no longer just a tool for innovation, but has become a fundamental and complex element…
Companies need AI to reinforce Zero Trust strategy
A new study by DXC Technology and Microsoft shows that although the Zero Trust model is becoming a…
The human firewall: how does the investment in cybersecurity training pay off in 3.5 months?
The collapse of a 158-year-old company due to a single broken employee password is a brutal reminder that…
Chinese hackers in the F5 code? IT industry reacts to another supply chain hit
The hacker attack on F5 Networks, one of the key providers of network security solutions for Fortune 500…
Poland in the TOP 10 most frequently attacked countries in Europe – Microsoft report
Poland is among the most attacked countries in Europe, as confirmed by the latest Microsoft Digital Defense Report.…
Cyber security in banking: AI looks at your behaviour, not your password
Digital fraud is no longer an isolated incident but has become a permanent feature of the financial landscape—it…
F5 hacked: Risks to global networks and IT infrastructure
The attack on F5, one of the key providers of cybersecurity solutions, shows that even the guardians of…
British business is breaking under the onslaught of cyber attacks. Government appeals to companies
British companies are facing an unprecedented wave of critical cyberattacks, which are increasingly paralyzing not only IT systems…
Security in FinTech: Analysis of the top 5 platforms in 2025
The FinTech sector is growing at an unprecedented rate, but each innovation brings with it new and increasingly…
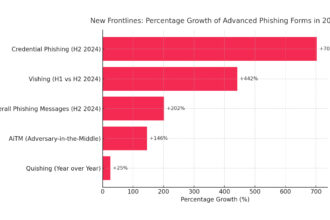
Phishing 2.0: How artificial intelligence is changing the cyber threat landscape
Artificial intelligence, combined with deepfake technology, is revolutionizing cybercrime, creating a new era of phishing known as Phishing…
Arrests after cyber attack on Kido nurseries. Hackers stole data of 8,000 children
British police have arrested two people in connection with a ransomware attack on the Kido International nursery chain,…
Public Wi-Fi versus your finances: A guide to online security
Using public Wi-Fi networks has become a symbol of modern flexibility, offering invaluable convenience in everyday work. However,…
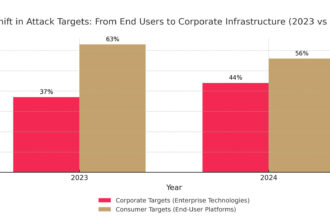
Anatomy of a zero-day attack: How hackers exploit unknown vulnerabilities and how to defend against it?
Attackers have changed their strategy, targeting not millions of users, but the heart of corporate infrastructure through unknown…
Generation Z raised on the internet most likely to fall for phishing
Contrary to popular belief, the generation raised in the digital world turns out to be the weakest link…
Orbotix raises €6.5m to develop AI-enabled military drones
The Polish-Romanian company Orbotix Industries has secured €6.5 million in funding for the development of autonomous drone systems…